Facebook “added friend confirmation” Malicious Spam
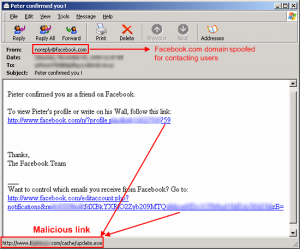
Websense Security Labs has discovered another round of malicious Facebook messages. This campaign is another visual social-engineering spam campaign which tries to visually trick users into believing that the message is a legitimate added friend confirmation. The “From” address in the message is spoofed to make it look as if it was sent from Facebook, and the links look like they lead to Facebook.
In previous Facebook “add friend” Malicious Spam campaign, spammers included a malicious zip attachment that claimed to contain a picture, to entice the recipient to double-click on it. From a spammer’s perspective, the likelihood of attack success decreases when antivirus software picks up the attachment. If not picked up by antivirus software, then content learning technologies filter such messages and their attachments after receiving a certain volume of similar messages.
In order to maintain their attack over a longer time period with increased success rates, spammers have switched their tactics by including links to an external Web site. The use of external links in emails makes antivirus detection tougher, as not all antivirus software has the ability to scan or detect links included in email messages. Also, from a spammer’s perspective, using links consisting of compromised ‘legitimate’ domains hosting malware as a lure increases the success rate, as this is more likely to bypass security filters that rely heavily on reputation services.
Websense Security Labs sees these tactics adopted by spammers and malware authors as an ongoing trend, increasingly targeting Web 2.0 sites to carry out a wide range of attacks.
Screenshot of the malicious Facebook message:
The links in the message actually lead to a malicious executable named “update.exe” (SHA1: a4dc17d1bcb191af75afedddf60aecbc2af2a37f).
This malicious executable has a very low AV detection. When run, the malicious executable steals data from its victim, establishing a connection with an IRC botnet.
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.