OpenX.org Used As An Intermediary For Malware, Possibly Spreading Exploits And Trojans
According to notifications from Google’s Safe Browsing service, openx.org, home to a leading open source ad server package, might be used as an intermediary for malware. In addition to developing the actual OpenX ad server software, the company also runs its own advertising network through which webmasters can sell advertising space on their websites.
The problem was observed by researchers from Web security company Sucuri, which provides a website integrity monitoring solution. “We are tracking a few sites that are currently blacklisted and showing a warning from Google that openx.org (home of a popular open source ad server) is the site responsible for the infection,” warns Sucuri researcher David Dede.
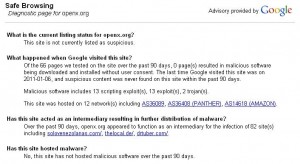
Indeed, the Google Safe Browsing diagnostic page for openx.org claims that “over the past 90 days, openx.org appeared to function as an intermediary for the infection of 82 site(s).”
This doesn’t mean that openx.org is hosting the malware itself, only that it is serving as a doorway. This could point to malicious ads being served via the OpenX network.
It certainly wouldn’t be the first time when cybercriminals manage to introduce malicious ads on an advertising network. Just recently there was a case where drive-by download attacks were launched via malvertizements served by Google and Microsoft.
OpenX also had malvertizing problems in the past, not through its ad network, but because of vulnerabilities in the software. Hackers exploited the security holes to compromise OpenX-based ad servers run by other websites and push malicious ads onto them.
A wave of such attacks took place in September and some of the victims included high profile sites like The Pirate Bay, Tucows, Popbitch.com, eSarcasm.com and AfterDawn.
“We are still tracking to see which ads are causing the issue, or if the openx servers themselves are compromised. If you include the tracking code from openx.org, we recommend that you check to see if there isn’t any malicious code being pushed to your users,” Sucuri advises.
Credit: Softpedia.com News
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.