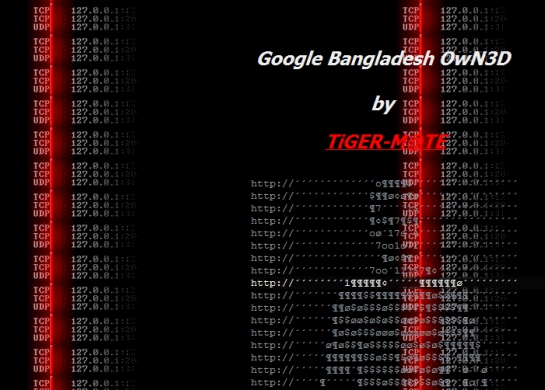
Google Bangladesh Google.com.bd DNS Hijacked, Redirects Visitors For A Limited Time
A hacker managed to hijack the DNS for google.com.bd and redirect the domain’s traffic to a website under their control for a limited period of time on Saturday. Many Bangladeshi Internet users reported being taken to a page saying that Google Bangladesh was “OwN3D by TiGER-M@TE.”
According to TechCrunch, Google confirmed the incident, but claimed the problem occurred at the Bangladesh Telecommunications Company which administers the .bd domain zone. TechIt reports the hijacking occurring only for google.com.bd, with www.google.com.bd continuing to display Google’s real website. Under normal circumstances, requests made to google.com.bd are automatically redirected to www.google.com.bd. It looks like someone intervened in that process.
No details are available about the method used to alter or poison the DNS entries for Google’s domain, but according to Web defacement archive Zone-H, TiGER-M@TE is responsible for attacks against many Bangladeshi websites.
These include www.waridtel.com.bd and www.bd.airtel.com, which belong to the Airtel telecommunications provider, as well as americanexpress.com.bd, the local branch of American Express.
DNS or domain hijacking incidents are not uncommon. In fact, their number appears to have increased during the past two years, especially for those involving high profile websites. Last month fraudsters hijacked the domain name of ChronoPay, the largest online payment processor in Russia and used the opportunity to phish credit card information.
In November, hackers managed to alter the DNS records for secunia.com, the domain name of one of the world’s leading vulnerability research firms. Other companies affected by similar attacks include Tata Consultancy Services (TCS), the largest IT and outsourcing provider in India, Baidu, the largest search engine in China, Twitter and Comcast, the largest US ISP.
The methods used to carry out these hijackings vary, but usually attackers rely on social engineering to trick employees at domain registrars to hand over control of the domains by posing as the real owners.
Credit: Softpedia.com News
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.