Classmates Users Hit By Network Sniffing Passwords Stealing Worm
Websense Security Labs reported yesterday a campaign against Classmates Online, Inc had broken out. Thousands of URLs were registered in one day to spread the worm. The newly-registered URLs were unusually long, had several subdomains, and always contained some specific words such as “process” and “multipart”.
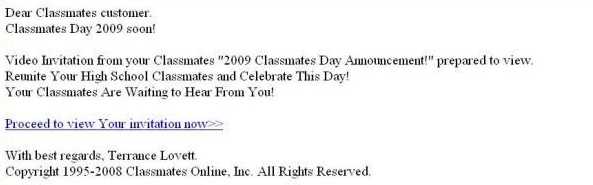
The new campaign was spread by email. The malicious email contained a link to a video invitation to reunite high school classmates and celebrate Classmates Day 2009.
When the email recipient viewed the invitation, they downloaded a worm named Adobe_Player10.exe. This could fool a user into thinking they needed the latest version of the Adobe Player, prompting them to run the executable.
Simple analysis showed that the main purpose of this worm was to steal user information and send it to a server located in the Ukraine. The address of the server was hardcoded in the worm. The worm did a lot of work, including dropping a driver file to hide itself, injecting itself into every process, downloads and so on. It collected several kinds of information, including details about POP3, IMAP, ICQ, FTP, and certification from the user’s MY certificate store, which is used to store trusted sites and personal certificates.
A network sniffer was also found in the worm that could monitor the network traffic. The worm searched for special keywords in the network flow such as “RCPT TO:”, “MAIL FROM:”, the two keywords used for SMTP protocol. When the malware found one of these keywords in the network traffic, it would parse some useful information such as the email address, username, and password, then send the details to the hardcoded server: in this case, http://91.********.57/cgi-bin/forms.cgi
The worm injected itself in every process. The injected code would enum a module of the process, and then hook some APIs into the module in order to monitor the network traffic to steal usernames and passwords for FTP and HTTP sessions.
Credit: Websense® Security Labs™ ThreatSeeker™ Network
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.