Cross-Site Scripting Vulnerability On Dogpile.com Helps Malware Spam Distributors
Over the last few months endless malware campaigns abused Google and DoubleClick redirect links in their spam. Clicking on such safe looking link will result a redirection to a malware hosting site and an infection of user’s Windows running machine.
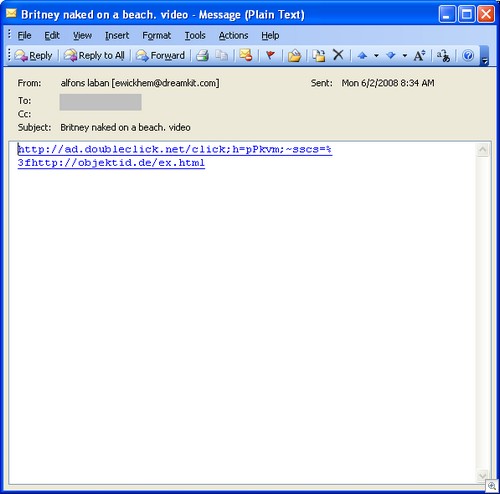
Even though it took Google some time to close this redirection, the malware authors have successfully switched to Dogpile.com redirection vulnerability. Here is an example of Dogpile.com cross-site scripting vulnerablity that allows redirection of visitors who click a link originating from dogpile.com domain:
http://www.dogpile.com/clickserver/_iceUrlFlag=1?
rawURL=http://CNN.com&0=
It is safe clicking on this link, it will just redirect you to CNN.com. Malware authors are actively using this redirection to infect users by sending them confusing, safe looking links to exploit hosting sites. The sad thing about it is that another redirection vulnerability on Dogpile was discovered and reported back in Novermber 2007. It is still unfixed.
Google has done quite a bit to fix the redirection problem, Dogpile should aslo fix it soon (hopefully), but the party will just move on to a different location. A good example would be a redirection vulnerability on Devicelock.com, reported by XSSed and still unfixed.
DeviceLock, Inc. is a “worldwide leader in endpoint device control security” and on their website they offer a security solution that prevents unauthorized access to USB devices. They are proudly using a Content Managment System (CMS) called Bitrix and here is the redirection example on their website:
Lets say an average user is receiving an email with a link like the one above. The email says that he is a winner of some free DeviceLock promotional product and all he needs to do to claim it is clicking that link. User clicks the link, being redirected to a malware hosting site and another Windows machine probably gets infected. Although the number of popular and trusted domains is limited, it seems malware spam techniques will contain various redirection links for a long time.
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.