Fake Wordpresz.org Site Distributes Backdoored WordPress Package
Wordpresz.org is a malicious website that is distributing a purposely backdoored, fake 2.6.4 version of WordPress. The fake package allows the theft of cookies from those who have installed it, potentially leading to hijacking of their WordPress blogging platforms for malicious purposes. The fake Wordpresz.org domain registered several days ago and shares it’s IP (209.160.33.108) with a fake online pharmacy – livepills.com.
The rogue WordPress site’s WHOIS records show:
Domain ID:D154583784-LROR
Domain Name:WORDPRESZ.ORG
Created On:31-Oct-2008 01:59:20 UTC
Last Updated On:31-Oct-2008 19:27:37 UTC
Expiration Date:31-Oct-2009 01:59:20 UTC
Sponsoring Registrar:EstDomains, Inc. (R1345-LROR)
Status:CLIENT TRANSFER PROHIBITED
Status:TRANSFER PROHIBITED
Registrant ID:DI_8908485
Registrant Name:Don T. Smith
Registrant Organization:N/A
Registrant Street1:2092 Village View Drive
Registrant Street2:
Registrant Street3:
Registrant City:Fort Myers
Registrant State/Province:Florida
Registrant Postal Code:33901
Registrant Country:US
Registrant Phone:+239.8469373
Registrant Phone Ext.:
Registrant FAX:
Registrant FAX Ext.:
Registrant Email: [email protected]
Admin ID:DI_8908485
Admin Name:Don T. Smith
Admin Organization:N/A
Admin Street1:2092 Village View Drive
Admin Street2:
Admin Street3:
Admin City:Fort Myers
Admin State/Province:Florida
Admin Postal Code:33901
Admin Country:US
Admin Phone:+239.8469373
Admin Phone Ext.:
Admin FAX:
Admin FAX Ext.:
Admin Email: [email protected]
Tech ID:DI_8908485
Tech Name:Don T. Smith
Tech Organization:N/A
Tech Street1:2092 Village View Drive
Tech Street2:
Tech Street3:
Tech City:Fort Myers
Tech State/Province:Florida
Tech Postal Code:33901
Tech Country:US
Tech Phone:+239.8469373
Tech Phone Ext.:
Tech FAX:
Tech FAX Ext.:
Tech Email: [email protected]
Name Server:NS1.WORDPRESZ.ORG
Name Server:NS2.WORDPRESZ.ORG
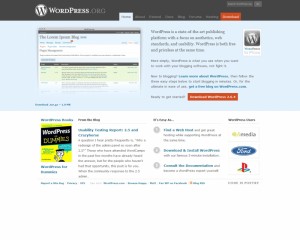
Fake site screenshot:
The domain registrar (EstDomains, used by spammers) and email name (“pismo”, which means “letter”) might indicate some Russian roots in this little scam.
According to Craig Murphy’s alert issued on Monday, when he logged in to his admin account in WordPress he received a “High Risk Vulnerability Warning” from a spoofed WordPress domain, Wordpresz.org. The warning suggests upgrading to the ‘new’ version 2.6.4 of WordPress. In this ‘new’ version there are 638 files, 637 of them were identical to the same files in the official 2.6.3. The only difference was in the file pluggable.php. The hacked version of the file pluggable appears to be stealing the content of cookies on larger installations of WordPress. Sophos are now detecting this file as Troj/WPHack-A.
The backdoored pluggable.php file attempts to send the stolen data to wordpresz.org/tuk.php which is still accepting cookies if the requests are properly formatted. The spoof is a nearly perfect combination of social engineering and typosquatting.
Peter Westwood, one of WordPress’s lead developers, responded to The Register requests for comment on the attack, which he reckons relies on exploiting older (vulnerable) code.
It looks like sites which have not upgraded to 2.6.3 are being exploited in an interesting way whereby a hacker, probably using an automated script, is hacking into sites with the vulnerability and changing the settings of one of the dashboard modules to point to a different feed thereby encouraging people to go to a different site which is offering a dodgy upgrade.
“We recommend that people upgrade as soon as possible when we release a security release so as to ensure they are not vulnerable to issues which will likely have exploits in the wild.
Also in the upcoming 2.7 release of WordPress we are including a built-in upgrade mechanism within WordPress which will allow people to upgrade automatically with ease. I would however stress the need with any piece of software to check that an upgrade is real by visiting the website of the software provider manually rather than relying on a link that you have been provided. Otherwise, as with bank phishing scams there is the potential for someone to trick you into doing something you didn’t want to do.
The latest version of WordPress (version 2.6.3), published on 23 October, is available through WordPress.org.
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.