Hackers Deface TechCrunch.com And Abuse Admins
Popular technology site TechCrunch was hit by hackers late on Monday, leaving the site temporarily unavailable.
A notice on TechCrunch.com’s front page on Tuesday morning explains that “TechCrunch.com was compromised by a security exploit”. Access to the site’s story archive has been suspended leaving a two para notice on the hack as the only content visible on the site.
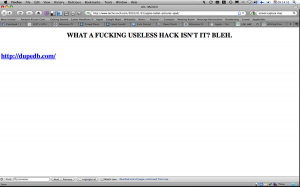
Hackers defaced the front page of the site with a message (recorded by Mikko Hypponen of F-Secure) apparently abusing site admins and including a link to a pornographic content and warez linking website.
The problems began for TechCrunch at around 10:30 pm PST on Monday when unknown hackers modified its home page to only display the word “hi.” The page was later changed to read “We’ll be back shortly,” suggesting that webmasters regained control of the website.
After a while, the site was hacked again and a link called “rapidshare downloads” appeared on the home page. The link actually pointed to DupeDB, a known warez website and was subsequently replaced by a “We’ll be back soon” message.
Hackers took over TechCrunch for a third time and left one offensive message accompanied by a link to the illegal content distribution site mentioned before. A final message from staff after this attack was also repelled, saying “Earlier tonight techcrunch.com was compromised by a security exploit. We’re working to identify the exploit and will bring the site back online shortly.”
Specific technical details regarding the incident are lacking, but a DNS hijacking attack similar to those experienced by Twitter and Baidu is out of the question. According to some sources cited by Praetorian Prefect, TechCrunch was using WordPress 2.8.4 at the time of the incident and 2.9.1 after. This apparent platform upgrade suggests that a WordPress vulnerability might have been exploited.
This defacement was removed by site admins who are in the process of identifying the exploit involved in the hack, securing systems, and bringing TechCrunch back online.
The motives or perpetrators of the attack remain unclear but the timing – a day before Apple’s much anticipated iTab launch in San Francisco – could hardly be worse.
TechCrunch returned to business by Tuesday lunchtime. The site has published a story on the attack, which is still under investigation. Hackers redirected traffic as well as leaving a defacement, TechCrunch explains.
Update (Jan. 27): TechCrunch has been hit by potty-mouth hackers for the second time in 24 hours. The second hack features a foul-mouth rant aimed against site founder Michael Arrington. It also includes a link to the same online smut and warez-peddling Torrents site “promoted” via the previous attack.
Credit: The Register, Softpedia.com News
More on CyberInsecure:












 Posts
Posts





January 26th, 2010 at 5:57 pm
TechCrunch getting hacked isn’t really big news. In fact websites getting hacked is so common now everyone is used to it. You just expect to get hacked… 🙂