Royal Bank of Canada Phishing
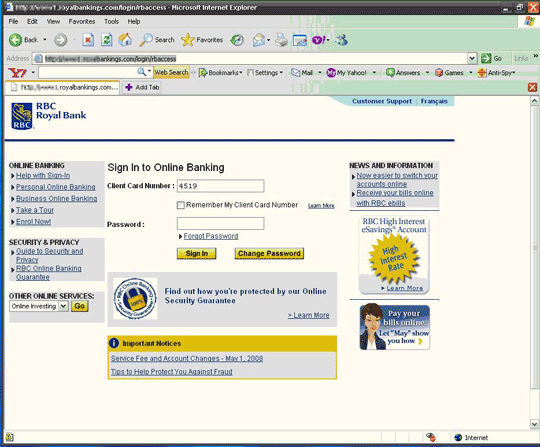
Another phishing Web site attempts to steal confidential credit card information. Using string manipulation, it is able to spoof the official Web site of the Royal Bank of Canada. Note that the said URL contains a variation on the actual domain name (“banking” vs. “bank”) to trick the users into thinking that it is the official Web site of the affected bank.
Screenshot of the phishing website, click to enlarge:
The spoofed URL masks the actual phishing URL by using a certain frame source. This frame source URL is responsible for gathering account-related information, such as credit card numbers and account passwords, from the affected users.
When the first frame source URL is blocked, a second frame source is used. The next time the phishing Web site is visited, it already uses another frame source URL. This is clearly a distinct approach in circumventing security restrictions related to phishing attacks.
The domain used by this phishing Web site is registered for just one year, which is highly unlikely since legitimate websites intend to operate for longer than that.
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.