Twitter Worm Outbreak Over Easter, XSS Flaw Remains Unfixed
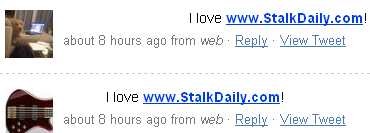
A cross-site scripting worm was spreading in Twitter profiles for several hours during April 12. People started reporting that their profile had sent Twitter messages without their knowledge. Messages looked like this:
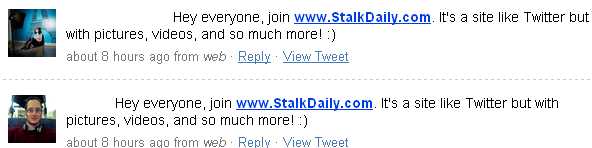
Later on the messages morphed several times:
Many people followed the links to promoted website, as they believed the messages to be genuine Tweets from their friends. A cross-site script on the site then caused new users to start to Tweet the same messages.
It is unclear if the spammed site was actually associated with the worm.
According to an explanation on DCortesi blog:
What’s happening here is that it looks like somebody realized they could save url encoded data to the profile URL field that would not be properly escaped when re-displayed. This is particularly nasty because you could get infected simply by viewing somebody’s profile page on Twitter that was already infected. If you visited an infected profile, the JavaScript in the profile would execute and by doing so tweet the mis-leading link, and update your profile with the same malicious JavaScript thereby infecting anybody that then visits your profile on twitter.com.
It looked like Twitter fixed the issue but another round of the worm hit Twitter on Sunday morning. It was effectively the same thing, but attacked a different field. Here’s of the current variants:
Besides the “original” worm that was supposedly written by a teenager, there are some copycats out. The code had also been run through an obfuscator. The copycat Twitter XSS worms exploit the same vulnerability and actually most of the code remains the same. The new version got obfuscated to make analysis a bit harder.
It looks like the folks from Twitter are still fixing all the vulnerabilities so seems that there’s going to be quite a few modified Twitter worms for a day or two. Twitter stats blog said that they are currently addressing a new manifestation of the worm attack.
No passwords, phone numbers, or other sensitive information were compromised as part of this renewed attack, according to Twitter.
All these attacks are Javascript-based so it is possible to turn Javascript off if you’re worried or use a NoScript Firefox add-on.
F-Secure detects the script file as Worm:JS/Twettir.A.
Credit and screenshots: Mikko, F-Secure Weblog
Credit: DCortesi.com Blog
Credit: SANS Internet Storm Center
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.