Google Video Search Results Poisoned To Serve Malware
According to ZDnet, during the last couple of days, a single group involved in a countless number of blackhat SEO campaigns across the Web, started massively targeting Google Video with a campaign that has already managed to hijack approximately 400,000 search queries in order to trick users into visiting a bogus and malware serving (W32/AutoTDSS.BNA!worm) adult web site. There are attempts to cloak the campaign from the eyes of security researchers.
This campaign relying entirely on Google Video traffic. Instead of sticking to the adult content in their keywords inventory, the cybercriminals have been in fact syndicating legitimate YouTube video titles from a variety of topics. Therefore, the number of legitimate videos used is proportional to the comprehensiveness of the campaign, in this case, over 400,000 search queries, a number that is increasing in real-time since they keep having their bogus content crawled by Google Video.
Moreover, based on the fact that they maintain a portfolio of 21 publisher domains with bogus and non-existent video content currently crawled, a simple tactic that they’re using could entirely hijack a search query at Google Video. Duplicating the content on their publisher domains, the top 5 search results for a particular video can be easily served from any of the 21 publisher domains, making it look like different sites have the same content.
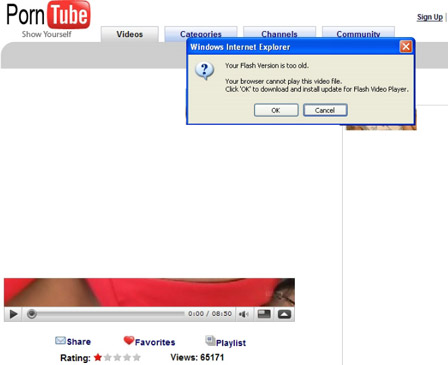
The search engine results poisoning works as follows. Upon clicking, a Google Video user coming across to any content from any of their 21 publisher domains, is taken to a single redirection point (porncowboys .net/continue.php), then to the well known adult site template abused by cybercriminals (xfucked .org/video.php?genre=babes&id=7375), where the user is told that “Your Flash Version is too old. Your browser cannot play this file. Click “OK” to download and install update for Flash Video Player” and the malware is served if he’s tricked into it (trackgame .net/download/FlashPlayer.v3.181.exe).
The cybercriminals are also taking advantage of a well known evasive technique – http referrer checking or “cloaked maliciousness. For instance, the malware redirection to the fake flash player is only served if the potential victim is coming from Google Video. If a researcher is basically browsing around the content of their sites, the legitimate YouTube videos are legitimately syndicated. Excluding this case, it’s worth pointing out that on the majority of occasions cybercriminals do not fully take advantage of the evasive features available within the traffic management kits they use behind the campaigns, making their campaigns easier for analyzing.
Google’s Security Team has been notified and action is expected to be taken anytime now.
Credit: Dancho Danchev, ZDnet BLogs
More on CyberInsecure:











 Posts
Posts





Leave a Reply
Comments with unsolicited links to other resources will be marked as spam. DO NOT leave links in comments. Please leave your real email, it wont be published.